3
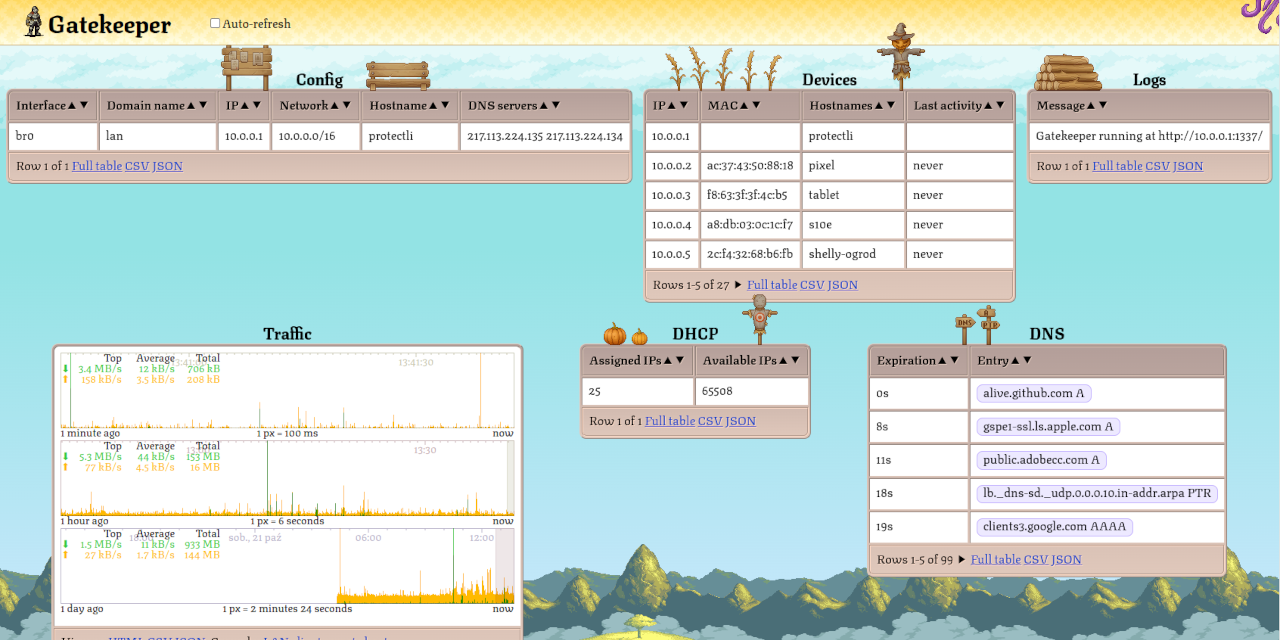
I've just released Gatekeeper 1.6.0. It's a single executable that turns any Linux machine into a home gateway. Now with realtime traffic graphs, LAN autoconfiguration, full cone NAT & better looks. - szmer
szmer.infoHi all home network administrators :) Haven’t posted anything here since June,
when I told you about Gatekeeper 1.1.0. Back then it was a pretty bare-bones
(and maybe slightly buggy) DNS + DHCP server with a web UI with a list of LAN
clients. Back at 1.1.0 Gatekeeper didn’t even configure your LAN interface or
set up NAT rules. It used to be something like dnsmasq - but with a web UI. I’ve
been improving it for the past couple of months - simplified it a lot, fixed
bugs, optimized internals, improved the looks & added a bunch of quality-of-life
features. Now it’s a program that instantly turns any linux machine into a home
internet gateway. It’s closer to OpenWRT in single executable file. One big
thing that happend was that I’ve attempted to replace the ubiquitous nft-based
NAT (where the kernel processes the packets according to a rule-based script)
with nfqueue (where the kernel sends the packet to userspace so that it can be
altered arbitrarily in regular C++). I’ve expected this to be buggy & slow.
Well, it was hell to implement but it turns out that it’s not slow at all. On
the debug build my router can push 60GiB+ / second over TCP (over virtualized
ethernet of course). And I’m not even using any io_uring magic yet. Quite
honestly I don’t even know how to explain it since it’s slightly above the peak
DDR4 transfer rate (I’m running dual channel DDR4-3200). Maybe the pages are not
flushed to RAM & are only exchanged through CPU caches? Anyway I’m pretty
excited because userspace access to all traffic opens a lot of new
possibilities… The first thing is NAT. By default Linux only supports symmetric
NAT, which is pretty secure but is also fairly hard for the peer-to-peer
protocols to pierce. There are some patches that make Linux full-cone but
they’re not, and are not expected to become a part of the mainline kernel (at
least according to OpenWRT forums). The workaround that everybody used for the
past decades is based on manual port forwarding. They work although they also
require manual setup. Now, since we have access to every packet we can take care
of this ourselves. We can create a couple hash tables to track connections,
alter the source & destination IP, recomputing the checksums if necessary.
Suddenly we can have full-cone NAT, on any linux machine, without patching the
kernel! At runtime it’s not as configurable as netfilter + conntrack but it’s a
whole lot simpler - since now we can use a general purpose programming language
rather than netfilter rules. Another cool feature that we can now have are truly
realtime traffic graphs. Summary of each packet traversing the network boundary
is immediately streamed to the connected web UIs over WebSocket. This is way
faster than the alternatives based on reading some /proc/ or /sys/ files every
couple of seconds. Gatekeeper also aggregates the traffic from the last 24 hours
between each pair of hosts into a histogram with 100ms resolution and allow
clients to view it, scroll through it, compute stats, download as JSON or CSV.
You can retroactively check which device talked with what IP, at what time with
unprecedented resolution. My next step is going to be capturing the traffic that
goes through into a 5MB circular buffer (separate buffer for each LAN client) &
downloading it as Wireshark-compatible pcap files. Computationally it’s almost
free. IoT devices usually don’t transmit a lot of data. 5MB may actually cover
months of traffic for the simpler ones. If any device is did anything weird, it
will finally be possible to investigate it - even after it already happened.
Long-term Gatekeeper could do even more. For example offer assistance in setting
up TLS MITM, perform some online grouping / analysis on the live traffic or
simply block ads. I still have some ground work to do - like automatically
setting up Wireless LAN, bridgidng multiple interfaces into a single one and I
think there may be a bug that causes crashes when checking GitHub for updates.
But I wanted to share it sooner rather than later. I hope that despite its
imperfections some of you will find it useful!
Hej, wrzuciłem posta przez Szmer, z docelową instancją Selfhosted@lemmy.world: https://szmer.info/post/1207883. Już kiedyś coś takiego robiłem i zadziałało ok (przykład: https://szmer.info/post/361728). Tym razem mój post nie pojawia się na docelowej instancji, choć z perspektywy szmer.info, pokazuje się w widoku najnowszych wątków.
Czy wiecie o co może chodzić?


No nie ma :)
Chodzi o to, że postuję przez szmer.info, jako @maf, ale post skierowany jest do lemmy.world. Więc serwer (“instancja” w lingo lemmiego) szmeru powinna założyć nowy wątek na lemmy.world
Z tego co wiem, druga instancja powinna widzieć wpis jeśli tam ktoś subskrybuje społeczność, do której wrzucasz ten wpis na Szmerze. Masz pewność, że ktoś tam ją subskrybuje?
Problem znaleziony! Lemmy ma limit 200 znaków na tytuł posta. Wersja 0.18.5 (na lemmy.world) zamienia znaki
&na&. Wersja 0.18.1 (na szmer.info) tego nie robi. Dlatego post na szmerze wrzucił się bez problemu (tytuł miał 198 znaków), ale lemmy.world odrzuciło go przez zbyt długi tytuł.https://github.com/LemmyNet/lemmy/issues/4080
O kurde, niezłe śledztwo musiało tam być. 😲